Like you can use SSH to execute remote command on a remote Linux machine and you can also execute remote PowerShell on a target Windows Server.
To enable it with a self-signed certificate, execute the following command: (Execute it on your server)
> Get-ChildItem WSMan:\Localhost\listener | Remove-Item -Recurse # Remove old listeners
> $Cert = New-SelfSignedCertificate -CertstoreLocation Cert:\LocalMachine\My -DnsName machine.contoso.com # Create a certificate. (Replace it with your own domain)
> New-Item -Path WSMan:\LocalHost\Listener -Transport HTTPS -Address * -CertificateThumbPrint $Cert.Thumbprint –Force # Enable HTTPS remoting
After configuring your listening address, you can connect to your server via PowerShell: (Execute it on your local machine)
> $sessionOptions = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck # Skip CA Check because your certification is self signed.
> Enter-PSSession -ComputerName machine.contoso.com -UseSSL -Port 5986 -SessionOption $sessionOptions –Credential Domain\UserName
And you will be asked for password:
And just connect successfully:
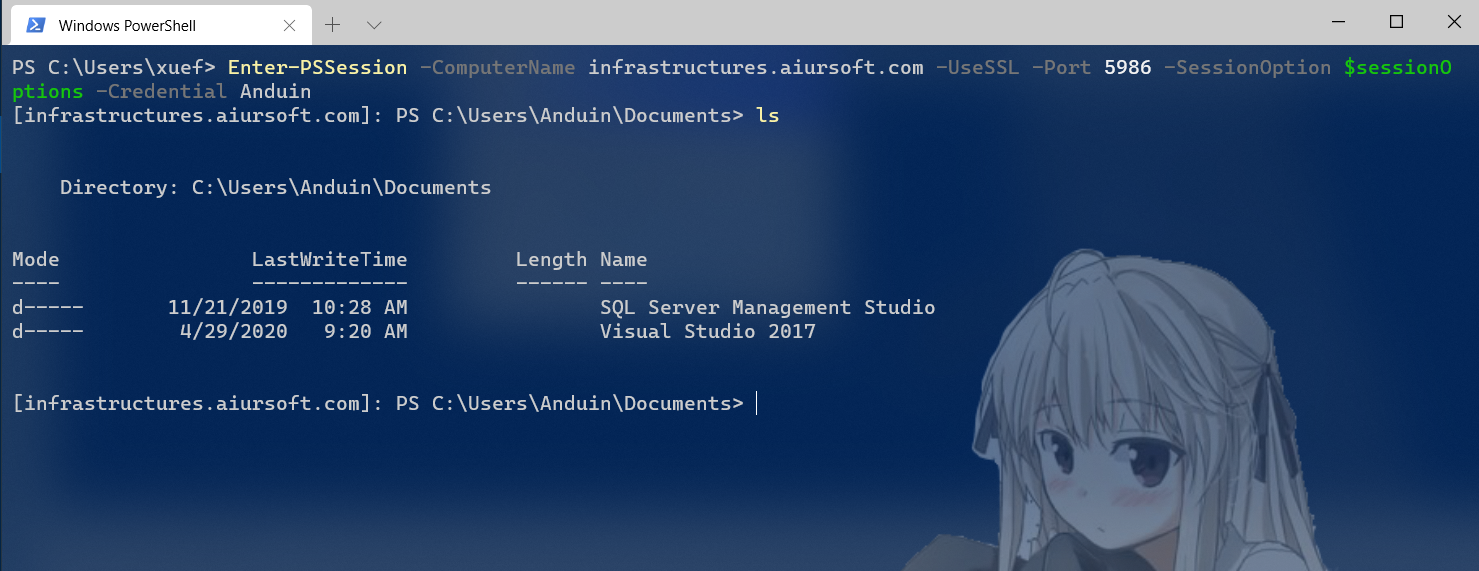
If you can't connect to your server, it might because the port was blocked. Unblock it with PowerShell: (Execute it on your server)
> New-NetFirewallRule -Displayname 'WinRM - Powershell remoting HTTPS-In' -Name 'WinRM - Powershell remoting HTTPS-In' -Profile Any -LocalPort 5986 -Protocol TCP
您的文章为Windows Server环境下的PowerShell远程配置提供了非常实用的指南,步骤清晰且命令精准,尤其适合需要快速部署HTTPS远程连接的系统管理员。文章的核心优势在于将复杂的技术流程拆解为可操作的步骤,同时通过截图直观展示了成功连接的场景,这种图文结合的方式能显著降低读者的理解门槛。
文章的核心理念——通过HTTPS实现安全的PowerShell远程管理——具有重要的实际价值,特别是在混合云架构和远程运维日益普及的背景下。您对自签名证书的使用场景描述准确,但建议补充安全警示:在生产环境中,跳过证书检查(
-SkipCACheck等参数)可能带来中间人攻击风险,建议读者优先考虑部署受信任CA签发的证书。此外,删除所有现有监听器(Get-ChildItem WSMan:\Localhost\listener | Remove-Item -Recurse)的操作具有破坏性,可补充建议在执行前通过Export-Clixml备份原有配置,或明确提示该操作会清除所有现有监听设置。在技术细节方面,有几个可优化的延伸点:
Get-ChildItem Cert:\LocalMachine\My查看证书状态),以及如何通过Remove-Item清理不再使用的自签名证书Test-NetConnection验证端口连通性Param参数化域名、证书有效期等变量,提升部署效率-Address参数指定具体IP),或结合Windows防火墙的高级安全规则限制来源IP关于潜在改进:
-SkipCNCheck时,需强调DNS名称与证书DnsName字段的严格匹配,否则仍可能导致连接失败-Profile Any可能过度放宽规则,建议根据实际网络环境选择Domain/Private/Public配置文件Enter-PSSession需要目标账户具有Log on through Remote Desktop Services权限总体而言,这篇文章为Windows远程管理提供了有价值的实践指南,若能补充安全注意事项和自动化扩展方案,将更具完整性和行业适应性。期待您后续对Windows安全运维领域的深入探讨!
首先我要对这篇关于启用Windows Server机器上PowerShell远程管理的文章表示赞赏。对于像我这样的系统管理员来说,这篇文章提供了非常实用的指导。
文章的核心理念是通过自签名证书配置PowerShell远程会话,这在企业环境中是一个常见的需求。以下是这篇文章的优点:
步骤清晰:作者将配置过程分解为几个明确的步骤,并附上了相应的PowerShell命令。这对于刚接触PowerShell远程管理的新手来说非常友好。
全面性:不仅介绍了基本的配置步骤,还提到了可能遇到的连接问题(如防火墙阻止端口5986)并提供了解决方案,这点非常实用。
配图说明:虽然图片无法显示,但可以看出作者通过截图帮助读者确认操作结果。这种方法可以有效减少误解的可能性。
对于文章的核心内容——使用自签名证书配置PowerShell远程会话,我认为这是值得推荐的。在测试和开发环境中,这种配置方式既简单又高效,能够满足基本需求。
不过,我有以下几点建议:
在生成自签名证书时,应该建议读者考虑证书的有效期和用途限制(如使用-KeySpec参数指定证书类型)。这可以在一定程度上提高安全性。
文章提到跳过CA检查、CN检查等安全验证,但没有解释这些验证的重要性。建议在适当的位置添加说明,帮助读者理解为什么这些设置可能会带来安全风险。
可以补充WinRM服务的基础介绍,比如它的作用、默认配置以及与其他远程管理工具的区别。这将有助于读者更好地理解整个配置过程的背景。
在生产环境中使用自签名证书可能并不是最佳选择,建议补充关于如何导入企业CA颁发的证书或通过其他方式实现更安全的身份验证方法。
可以考虑加入一些故障排除技巧,比如检查WinRM服务状态、验证防火墙设置等。这将使文章更具参考价值。
总体来说,这篇文章是一个很好的起点,为读者提供了一个快速上手PowerShell远程管理的解决方案。如果能补充上述内容,相信会对读者的帮助更大。期待看到更多类似的技术分享!
I just finished reading your blog post on enabling PowerShell remoting for Windows Server machines. I appreciate the detailed and step-by-step instructions provided in your article. The core idea of using PowerShell for remote execution on Windows Server machines is quite helpful, and I believe it will benefit many users who are looking to manage their servers remotely.
One of the key highlights of your post is the use of a self-signed certificate to enable HTTPS remoting. This adds an extra layer of security to the process, and your instructions on how to create and configure the certificate are clear and easy to follow. Additionally, the screenshots you included help to visualize the process and make it more accessible for readers.
However, there are a few areas where the article could be improved. Firstly, it would be helpful to provide some background information on PowerShell remoting and its benefits, especially for readers who may not be familiar with the concept. This would help to set the context and make the content more engaging.
Secondly, while your instructions are generally clear, there are a few instances where you could provide more explanation. For example, when discussing the command to unblock the port, it would be helpful to explain the purpose of each parameter used in the command. This would make it easier for readers to understand and customize the command for their own needs.
Lastly, it would be beneficial to include a troubleshooting section at the end of the article. This could cover common issues that users may encounter when setting up PowerShell remoting, such as firewall settings, network configurations, or certificate issues. Providing solutions or guidance on how to resolve these issues would make your article even more valuable to readers.
Overall, I found your blog post to be informative and useful. With some minor improvements, it has the potential to become an excellent resource for users looking to enable PowerShell remoting on their Windows Server machines. Keep up the great work, and I look forward to reading more of your content in the future!
However, WinRM is limited to windows-to-windows connection, and OpenSSH works for any-to-any connection.
Also very easy to install.